Introduction
In the world of cybersecurity, understanding the mechanics
of Distributed Denial of Service (DDoS) attacks is crucial for both offensive
and defensive strategies. While DDoS attacks can be malicious, simulating such
attacks in a controlled environment can help security professionals identify
vulnerabilities and strengthen defenses. In this blog post, we'll explore an
advanced DDoS simulation script written in Python using the powerful Scapy
library. This script allows penetration testers to simulate DDoS attacks using
various protocols, including TCP, UDP, and ICMP, while employing threading for
enhanced performance.
What is DDoS?
A DDoS attack aims to overwhelm a target system, service, or
network by flooding it with a massive volume of traffic, thereby rendering it
unavailable to legitimate users. Attackers often use botnets—networks of
compromised devices—to carry out these attacks. Understanding how these attacks
work is essential for developing effective mitigation strategies.
The Role of Scapy
Scapy is a Python-based interactive packet manipulation
program that allows users to create, send, and analyze network packets. It is a
versatile tool for network testing, security research, and penetration testing.
With Scapy, users can craft custom packets, making it an excellent choice for
simulating various types of network attacks, including DDoS.
Features of the Advanced DDoS Simulation Script
The advanced DDoS simulation script we will discuss
implements several features to enhance its functionality:
- Protocol
Selection: Users can choose between TCP, UDP, and ICMP protocols,
allowing for a more realistic simulation of different attack vectors.
- Threading:
The script utilizes Python's threading module to send packets
concurrently. This feature simulates the behavior of multiple attacking
machines, making the simulation more effective.
- Random
Source IPs: Each packet is sent with a randomly generated source IP
address, mimicking the behavior of a botnet and making it harder for
defenders to block the attack.
- Configurable
Parameters: Users can specify the number of threads and packets to
send per thread, providing flexibility in simulating different attack
intensities.
The Code
Here’s the complete code for the advanced DDoS simulation
script:
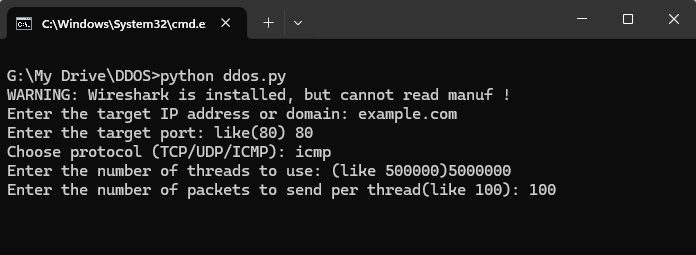
How to Use the Script
- Set
Up Your Environment: Ensure you have Python and Scapy installed. You
can install Scapy using pip:
pip install scapy
- Run
the Script: Execute the script in a controlled environment where you have
permission to perform testing.
- Input
Parameters: The script will prompt you for the target IP address or
domain, the target port, the desired protocol (TCP, UDP), the number of
threads, and the number of packets to send per thread.
- Analyze
the Results: Monitor the target system's response to understand how it
handles the simulated traffic. This can help identify potential
vulnerabilities and areas for improvement in network defenses.
Features of the Advanced Script:
- Protocol
Selection: You can choose between TCP, UDP, and ICMP protocols.
- Threading: The
script uses threading to send packets concurrently, simulating a more
realistic DDoS attack.
- Random
Source IPs: Each packet is sent with a randomly generated source
IP address.
- Configurable
Threads and Packets: You can specify the number of threads and
packets to send per thread.
Ethical Considerations
While simulating DDoS attacks can be a valuable exercise in
understanding network security, it is crucial to operate within legal and
ethical boundaries. Always ensure you have explicit permission from the system
owner before conducting any tests. Unauthorized testing can lead to severe
legal consequences and damage to systems.
Conclusion
Understanding DDoS attacks and how to simulate them using
Python and Scapy is an essential skill for cybersecurity professionals. The
advanced DDoS simulation script presented in this blog provides a comprehensive
tool for testing and improving network defenses. By utilizing various
protocols, threading, and randomization, this script allows for realistic
simulations that can aid in identifying vulnerabilities and enhancing security
measures.
As you explore the world of cybersecurity, remember to
prioritize ethical practices and always conduct testing in a controlled
environment with proper authorization. Happy testing!








3 Comments